As practice shows, the fewer users have access to a particular computer, the longer the system remains operational on it and the more likely it is that folders and files will be safe and sound. It is best if the computer has only one user. Alas, in reality this is far from always the case: at work you have to let other employees use your computer, at home quite often the same computer is used by all family members, and in public places (in particular, in educational institutions and computer clubs) the number of users computer can be very large.
About the need to restrict access
It is quite understandable that usually neither colleagues nor household members want to harm your computer, but if they belong to the category of novice users, then problems cannot be avoided. And the younger generation in educational institutions usually does not set themselves the goal of disabling the computer and destroying the information stored on it - they simply actively experiment, without thinking about what consequences certain actions can lead to.
As a result, certain problems inevitably arise on computers in the operation of individual applications or the operating system. This is not surprising, because it is enough to accidentally (simply by negligence or in the course of an experiment) delete, for example, a monitor driver - and the image on the screen will become less attractive, remove the printer - and printing documents will be impossible, change network settings - and the computer will stop working in the local networks, etc. And this is not the worst option - accidentally deleting a number of system folders and files can lead to a complete inoperability of the operating system, so it will have to be reinstalled. And the destruction of important working documents can have even more sad consequences - it is possible that it will not be possible to restore them in full and part of the work (or even all of it) will have to be done again. In addition, it cannot be discounted that if your personal or corporate materials are of any commercial value, attackers may want to use them.
Thus, the issue of restricting access to a computer, its individual devices, as well as the data stored on it, is to some extent relevant for all computer users without exception. It’s just that for some (administrators, teachers in computer classes with children of home users), the tasks of blocking access to operating system settings and protecting files and folders of the operating system and installed applications come to the fore, while for others (this includes administrators, specialists from computer departments). security and teachers, who in our country, along with teaching activities, are often also forced to ensure the operability of computers under their control) it is more important to block access to various devices (USB, CD / DVD, FireWire, etc.). There are three reasons for the need to block access to devices: firstly, it is on such devices that insiders often take confidential information from companies; secondly, viruses and Trojans often enter the computer through these devices; thirdly, various programs are installed from removable media, which is desirable to prevent - otherwise, in a week, such a number of toys will be installed on a computer, for example, in an educational institution, that there will simply be no room left for other applications.
Many office workers are interested in completely blocking access to a running computer in the absence of a legitimate user. The need for such protection in the office is very relevant, because even if you have your own computer, the user cannot be near him all the time and there are often situations when the computer is turned on unattended, which can be used by other employees interested in your materials.
Another group of users (it includes all office workers and home users) is concerned about the protection of personal data to prevent their damage, deletion or leakage. The problem of protecting personal folders and files inevitably arises when several people work at a computer. This can be at home, when you need to protect other family members (for example, a child) from information that is not intended for them, and at work, where even if each user has their own computer, situations are possible when another employee needs to perform some tasks on your computer. operations. In both cases, there is no need to show outsiders your working materials, and not at all because they are classified as “top secret”. Everything is much simpler: no one likes outsiders to interfere in their affairs. In addition, by blocking access to your folders and files, you can not worry that something will happen to them through the fault of another (insufficiently trained) user or they will be illegally used, which, unfortunately, is quite possible if the materials are of commercial value.
In general, the issue of reasonable access restriction is very complex and multifaceted, and it is impossible to solve it without suitable applications. This article is devoted to such applications.
Programs for restricting access
The range of applications offered on the market for restricting access is quite wide and covers diverse software products. Some of them block access to the operating system settings, others allow you to control access to various devices, others completely block the computer in the absence of the user, and the fourth ones provide hiding personal data. Often, these features are combined in one or another combination, which is quite understandable, because many users need to restrict access in several directions at once in order to solve the tasks they face.
Blocking access to operating system settings and system data
The built-in Windows tools allow you to impose some restrictions on user access to operating system settings and system data by managing the local security policy (Control Panel => Administrative Tools => Local Security Policy). In particular, you can prohibit changing the account password and installing printer drivers, limit the list of applications allowed to use, etc., but the list of restricted settings is limited.
At the same time, in practice, to ensure the stable operation of the system, it is often necessary to limit the capabilities of users more, which can only be done using highly specialized utilities designed to control access to a computer. As an example, we will consider the programs Security Administrator, WinLock, Deskman and My Simple Desktop. The most interesting of them is the Security Administrator utility, which allows you to restrict access to all important system settings and is aimed at system administrators. The My Simple Desktop program has the least functionality, but it is free for personal use and has quite sufficient capabilities for some home users, and you can master it in a matter of seconds.
Security Administrator 12.0
Developer: getfreefile
Distribution Size: 1.85 MB
Work under control: Windows 9x/Me/NT4/2000/XP/2003/Vista
Distribution method http://www.softheap.com/download/secagent.zip)
Price: $69
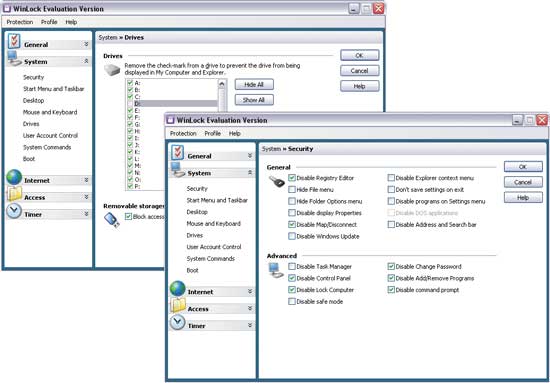
Security Administrator is a professional solution for managing access to a computer that allows you to restrict access to a computer and all its important settings (Fig. 1) both in general and for individual users. It is also possible to completely block the switched on PC in the absence of the user. In addition to setting restrictions, the utility can be used to control the work of users on the computer, since it keeps statistics on the use of the local network, the Internet, etc.
Rice. 1. Restrict access to system settings and hide drives
in Security Administrator
This solution is useful for setting a wide range of access restrictions. With it, it is easy to restrict access to desktop settings (prohibit changing display properties, hide certain icons, etc.) and disable some Start menu items, hide the taskbar (all or only certain elements). It also prohibits the installation/uninstallation of applications and restricts user options when browsing the Internet: prohibit changing Internet Explorer settings, downloading files, accessing the Internet from applications, etc. There are also ample opportunities to protect critical system settings from changes - for example, you can prohibit editing the system registry, activating DOS mode, installing new drivers, adding / removing printers, copying / moving files in system folders and deleting files and folders from the My Computer folder . And also hide the control panel, printers, network connections and the Run command from the Start menu. If necessary, the control panel can be hidden not completely, but partially, hiding the most critical elements from the point of view of unauthorized changes, such as "System", "Display Properties", "Network", "Passwords" and "Printers". It is just as easy to hide local, network and USB drives, disable burning and autoplay of CDs, block the use of Windows hotkeys and the launch of specific applications, as well as hide specified folders - these folders will become invisible in My Computer, Explorer and dialog boxes. windows of Open/Save Windows applications.
WinLock 5.0
Developer: Crystal Office Systems
Distribution Size: 2.65 MB
Work under control: Windows 95/98/Me/NT4.0/2000/XP/Vista
Distribution method: shareware (30 day demo - http://www.crystaloffice.com/winlock.exe)
Price: WinLock - $21.95; WinLock Professional - $31.95
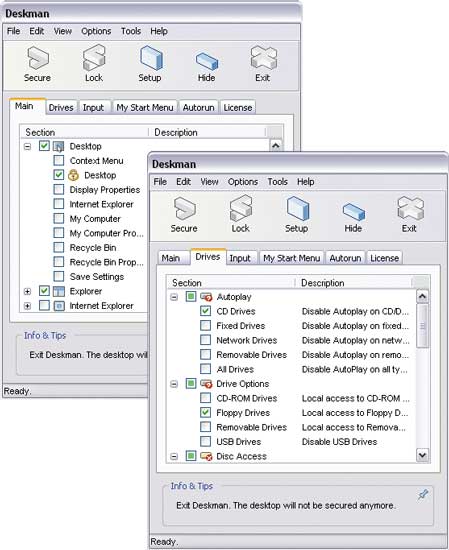
WinLock is a convenient solution for restricting access to important system resources (Fig. 2) and user data, including remote access. The program is presented in two versions: basic WinLock and extended WinLock Professional (the capabilities of the basic version do not allow restricting access to web resources and using encryption).
Rice. 2. Restrict access to system settings and hide drives
in WinLock
With this solution, you can disable access to the system registry, hide commands from the Start menu for accessing the control panel, printers and network connections, and completely block access to the corresponding system folders and to some other folders (My Computer, My Documents , basket, etc.). And also set a ban on blocking the computer and make it impossible to change the settings of the taskbar, display settings, network settings, add / remove programs from the Start menu and rename icons on the desktop. It's just as easy to set up prohibitions on activating DOS mode and booting Windows in safe mode and blocking Windows hotkeys (Alt+Ctrl+Del, Alt+Tab, Ctrl+Esc, etc.). If desired, you can even restrict the ability to manage windows (for example, prohibit resizing and moving them). The program also has tools for blocking access to removable media (CD / DVD drives, USB devices, etc.) and hiding the display of certain drives in the My Computer folder and Explorer. You can block the launch of specific applications (download managers, games, etc.) and deny access to certain files and folders (the former cannot be opened for viewing or editing, and the latter cannot be opened, renamed or deleted). And also prevent access to dubious web resources (based on the white list of allowed sites and the black list of prohibited keywords) and set limits on the time of using the computer by specific users.
Deskman 8.1
Developer: Anfibia Software
Distribution Size: 1.03 MB
Work under control: Windows 2000/2003/XP/Vista
Distribution method: shareware (30 day demo - http://www.anfibia-soft.com/download/deskmansetup.exe)
Price: personal license - 25 euros; business license - 35 euros
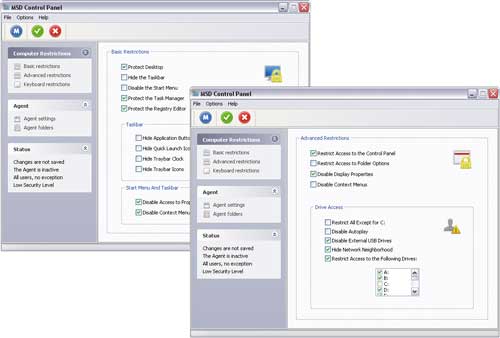
Deskman is a simple tool for controlling access to a computer and its settings (Fig. 3), which allows you to completely block the PC (including the keyboard, mouse and desktop) or restrict access to certain of its functions (individual restrictions are possible for different users).
Rice. 3. Setting limits in Deskman
Using this solution, you can restrict access to desktop settings (for example, prevent changing display properties, deleting icons, calling the context menu, etc.), Windows Explorer, the taskbar, Internet Explorer settings and prohibit changing various elements of the Start menu. And also restrict access to the control panel and other critical system settings - for example, prohibit the removal of network drives, block the restart and shutdown of the computer, etc. If necessary, it is easy to block all or only certain Windows hotkeys (Alt+Ctrl+Del, Alt+Tab, Ctrl+Esc, etc.) and configure the utility to automatically remove new entries from startup to prevent viruses, adware and spyware modules . It is possible to prohibit other users from using specific hard drives and removable media (CD / DVD drives, USB devices, disk drives, etc.), blocking autoplay of CDs and burning them. You can configure restrictions through pre-installed profiles (it is more convenient for beginners and much faster) or manually.
My Simple Desktop 2.0
Developer: Anfibia Software
Distribution Size: 1.76 MB
Work under control: Windows XP/Vista
Waydissemination: My Simple Desktop Office Edition and My Simple Desktop School Edition - shareware (30-day demo - http://www.mysimpledesktop.com/downloads.sm.htm); My Simple Desktop Home Edition - freeware (http://www.mysimpledesktop.com/download/msdsetup_home.exe)
Price: My Simple Desktop Office Edition - 32 euros; My Simple Desktop School Edition - 20 euros; My Simple Desktop Home Edition - free (for personal use only)
My Simple Desktop is a very simple program for restricting access to a computer and its settings (Fig. 4). It is presented in three editions: the paid My Simple Desktop Office Edition and My Simple Desktop School Edition and the free My Simple Desktop Home Edition (the possibilities of the editions are completely identical).
Rice. 4. Setting access restrictions in My Simple Desktop
With this utility, you can protect the desktop, taskbar and Start menu from changes, make it impossible to make changes to the display settings and the Explorer context menu. And also deny access to the control panel, folder properties and the system registry and block the use of Windows hot keys and the right mouse button. The device access restriction plan includes a ban on the use of fixed drives and external USB devices, as well as hiding network drives and blocking autoplay of CDs. If necessary, you can set a limit on the time of using the computer - the same for all users, except for the administrator. Restrictions are configured by assigning one of the preset profiles or manually.
Restrict access to devices
The built-in mechanisms for distributing access rights and setting security policies in operating systems of the Windows family (except Windows Vista) do not allow controlling other users' access to potentially dangerous devices (USB devices, CD / DVD drives, FireWire and infrared ports, etc.). Of course, you can disable such devices in the BIOS, but this is not an option, since to work with a disabled device (if necessary), you will have to access the BIOS each time and turn it on again, which is quite long and very inconvenient.
It is much wiser to control access to devices using additional applications, which can be very different. Often, the ability to hide or block devices is provided in utilities designed to control access to operating system settings, including those reviewed by us. True, the possibilities for restricting access to devices are not great in them: you can control access to far from all dangerous devices, and we are not even talking about media control. Much more functionality in this regard is provided by utilities - device access blockers and specialized solutions for protecting the system from leaks of corporate information. As an example, we will consider the DeviceLock, USB Lock Standard and ID Devices Lock programs. The most functional of them is the DeviceLock program, with which you can control (and not just block) the access of individual users and user groups to almost any potentially dangerous devices (and even media), but it is mainly aimed at system administrators. The capabilities of the other two utilities are much more modest, but they are quite enough for most users.
Device Lock 6.3
Developer: CJSC "Smart Line Inc"
Distribution Size: 39.7 MB
Work under control: Windows NT/2000/XP/Vista
Distribution method: shareware (30 day demo - http://www.devicelock.com/ru/dl/download.html)
Price: 1300 rub.
DeviceLock is a specialized solution for organizing a corporate information leakage protection system that allows you to control access to the entire range of potentially dangerous devices: USB ports, disk drives, CD / DVD drives, as well as FireWire, infrared, parallel and serial ports, Wi-Fi and Bluetooth adapters, tape drives, PDAs and smartphones, network and local printers, internal and external removable drives and hard drives. The program has a centralized remote control system that provides access to all functions from the workstation of the system administrator. Such management is implemented using the additional DeviceLock Enterprise Manager console or through Actvie Directory group policies, which allows you to automatically install DeviceLock on new computers connected to the corporate network and configure automatically for new computers.
Either a complete blocking of a certain type of device is possible, or partial, that is, in accordance with the white list of media (Fig. 5), in which access to some media will be allowed despite blocking the corresponding type of device. You can also set read-only mode and protect disks from accidental or intentional formatting. It is possible to assign different access rights to devices and I / O ports for individual users and user groups with the ability to set control depending on the time and day of the week. If necessary, you can log all user actions with devices and files (copying, reading, deleting, etc.) by performing shadow copying.
![]()
Rice. 5. Setting device access restrictions according to
with white list of media in DeviceLock
USB Lock Standard 3.4.1
Developer: Advanced Systems International S.A.C.
Distribution Size: 2.02 MB
Work under control: Windows XP/Vista
Distribution method: shareware (10 day demo - http://www.advansysperu.com/down_st.php)
Price: $44
USB Lock Standard is a convenient tool for blocking access (Fig. 6) to all types of removable media: USB ports (USB drives, iPods, MP3 players, etc.), Zip devices, floppy drives, CD / DVD drives, Bluetooth adapters and smart card readers (CF, SD, MMC, XD, etc.). It allows you to completely block access to the specified devices or do it partially by opening access for authorized devices. To cancel the blocking, you need to know the password or a USB key. Operations with unlocked devices are recorded in the logs.
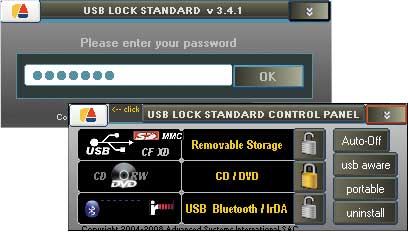
Rice. 6. Access blocking
to CD/DVD drives in USB Lock Standard
ID Devices Lock 1.2
Developer: ID Security Suite
Distribution Size: 1.47 MB
Work under control: Windows 98/NT/2000/XP/Vista
Distribution method http://www.idsecuritysuite.com/files/iddeviceslocksetup.exe)
Price: $37
ID Devices Lock is a simple utility for restricting access (Fig. 7) to USB devices, CD drives and drives by prohibiting copying data to them, which helps prevent information leakage on mobile media. To cancel the lock, you need to know the password.
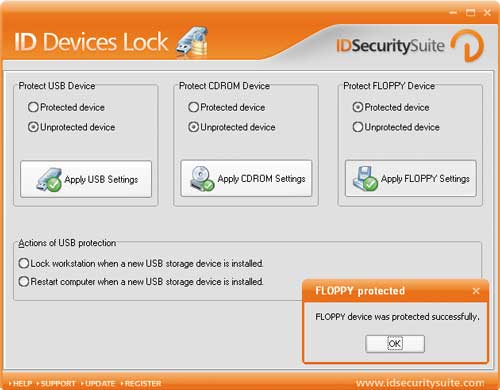
Rice. 7. Restricting access to the drive in ID Devices Lock
Complete blocking of the computer in the absence of the user
The easiest way to block access to a computer that is turned on is to set a password for the splash screen, but this is not the best option, since you can easily remove the password from the screen saver when you reboot. It is much more reliable to completely lock the computer using special software that will make it impossible to access any elements of the computer, including the keyboard, mouse and desktop. After that, it will no longer be possible to view any information on it, launch applications, access files and folders (including currently open ones), and even restart the computer by pressing the Ctrl + Alt + Del keyboard shortcut. You can unlock the computer only by knowing the user's password, and a simple reboot (even in safe mode) or a power failure will not lead to the removal of protection.
Such blocking of a computer is usually provided using highly specialized utilities: Desktop Lock, Lock My PC and similar, however, such opportunities can also be provided in programs designed to set various kinds of access restrictions, in particular, in Security Administrator and Deskman.
Desktop Lock 7.2.1
Developer: TopLangsoftware
Distribution Size: 792 KB
Work under control: Windows NT/2000/XP/2003/Vista
Distribution method: shareware (15 day demo - http://www.toplang.com/dlsetup.exe)
Price: $24.95
Desktop Lock is a utility for blocking a computer (Fig. 8) while the user is away. Blocking is set from the utility itself by pressing a certain key combination automatically at the time specified by the user or, if the user is inactive, after a specified period. Entering the computer into locked mode may be accompanied by the launch of a screensaver, playing an audio or video file, which is reasonable, for example, at exhibitions when demonstrating corporate presentations. Locking disables the mouse and makes it impossible to use basic keyboard shortcuts. To exit the locked mode, you need to press a secret keyboard combination or mouse button with a password. If desired, you can configure the utility to capture short messages from other users who approached the computer during the absence of its owner and wished to write something to him.
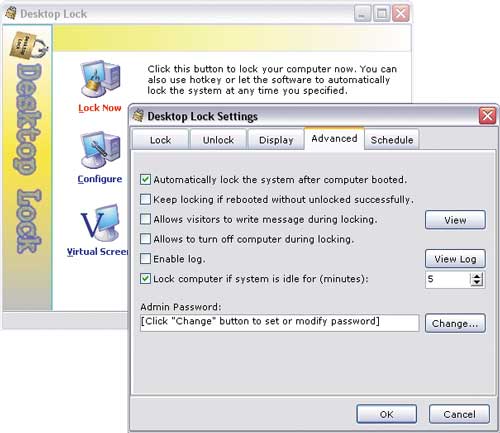
Rice. 8. Set Computer Lock Options in Desktop Lock
Lock My PC 4.7
Developer: FSPro Labs
Distribution Size: 1.4 MB
Work under control: Windows 2000/XP/2003/Vista
Distribution method: shareware (30-day demo - http://www.fsprolabs.com/download/distr/lmpc.zip)
Price: personal license - $19.95; business license - $29.95
Lock My PC is a tool for blocking a computer (Fig. 9) while the user is away. Locking a computer is easy - just double-click on the corresponding icon in the system tray or press a special keyboard combination. It is possible to automatically block after a specified time of user inactivity. When locked, the mouse and CD / DVD drives are turned off (this will not allow you to remove CDs from them) and it becomes impossible to use the main keyboard combinations: Ctrl + Alt + Del, Alt + Tab, etc. On a locked computer, any , including self-created images in GIF, JPEG, BMP and animated GIF formats. You can unlock the computer only if you know the user or administrator password.
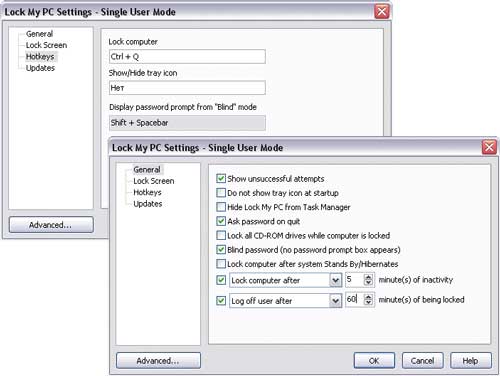
Rice. 9. Customize your computer lock settings in Lock My PC
Protection of personal information
There are several ways to protect personal data from unauthorized access: you can compress folders and files in a password-protected archive; hide them; put in a secret folder, access to which for other users will be protected by a password; encrypt or create a virtual encrypted disk, on which to record your secret materials. The choice of the most preferred method depends on the situation, but in most cases the best option is to hide and encrypt folders and files, so in this article we will limit ourselves to it.
Theoretically, you can hide folders and files using the built-in capabilities of Windows - for this, it is enough to enable the "Hidden" attribute in the properties of the corresponding objects. Folders and files hidden in this way will not be visible in Explorer to other users of the system, but only on condition that the "Do not show hidden files and folders" checkbox is enabled in the properties of the parent folders containing them. In principle, this may be enough to protect data from untrained users. However, objects hidden in this way will be visible in applications that do not use the standard dialog for displaying files and folders (FAR, Total Commander, etc.), so such protection is not very good.
A more reliable option for protecting data with the built-in Windows tools is to use the EFS (Encrypting File System, EFS) encrypted file system, which allows you to encrypt files by enabling the “Encrypt content to protect data” option for them in Explorer (Properties => General => Advanced). It is impossible to read files encrypted in this way without knowing the password, however, the EFS system allows you to protect folders and files only in the NTFS file system.
For these reasons, it is better to use specialized utilities to protect personal folders and files. These solutions will allow you to more securely hide folders and files (they will not be visible when you disable the checkbox "Do not show hidden files and folders"), as well as block access to them. Moreover, some of these utilities also provide the ability to encrypt data, which will ensure their protection from other users even when booting Windows in safe mode, booting into another operating system, or on another computer (if a hard drive with protected information is installed on it beforehand) . We'll look at Folder Lock, Folder Guard, and Hide Folders XP as examples. The first provides the highest level of protection for encrypted data, the second additionally provides tools to protect the basic OS settings from changes. The Hide Folders XP package is noticeably inferior to the named solutions in terms of its capabilities, but it has a Russian-language interface and is offered to Russian-speaking users at a very attractive price.
Folder Lock 6.0.1
Developer: NewSoftware Professionals, Inc.
Distribution Size: 2.78 MB
Work under control: Windows 2000/XP/2003/Vista
Distribution method: shareware (20 day demo - http://dl.filekicker.com/nc/file/130083-0M78/folder-lock.exe)
Price: $35.95
Folder Lock is an effective and reliable solution for protecting personal files, folders (Fig. 10) and drives by setting a password, hiding and encrypting them (AES algorithm with a 256-bit key). For greater security, this solution allows the use of blocking and encryption at the same time - files protected in this way are not displayed in Explorer and in applications and are completely inaccessible, since you cannot access them without knowing the password even if you boot into DOS, in Windows safe mode, from another OS or on another computer. In case the password is forgotten, it is possible to gain access to data using the registration key. The original data that needs to be protected can be located not only on the hard drive, but also on USB-drives, memory cards, CD-RW disks, floppy disks and laptops. And the installation process of the provided protection can be performed automatically in case of inactivity of the computer. In the special Stealth Mode, the program is able to hide all traces that indicate the installation of data protection on the computer: it prevents the display of its own shortcuts on the desktop and in the Start menu, hides installation / uninstallation data in the corresponding section of the control panel, clears the history and buffer data exchange, etc. In addition, for greater security, the program keeps a record of all passwords that were unsuccessfully entered to remove protection, which allows the user to timely record the manifestation of an unhealthy interest in his own computer from other users.
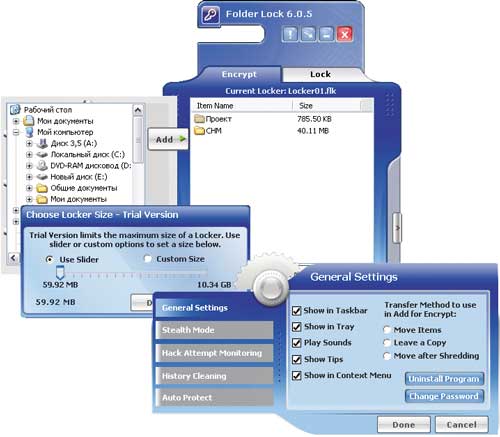
Rice. 10. Working with protected folders in the Folder Lock package
Folder Guard 7.6
Developer: WinAbility Software Corporation
Sizedistribution kit: Folder Guard Editions and Folder Guard x64 Edition - 1.8 MB; Folder Guard Professional Edition - 2.5 MB
Work under control: Windows 2K/XP/2003/Vista
Distribution method: shareware (30 day demo - http://www.winability.com/folderguard/editions.htm)
Price: Folder Guard Editions and Folder Guard x64 Edition - $39.95; Folder Guard Professional Edition - $59.95
Folder Guard is a simple and convenient solution for restricting access to folders and files, as well as preventing access to a number of Windows settings. It comes in three editions: Folder Guard Editions, Folder Guard x64 Edition and Folder Guard Professional Edition. The first version works on 32-bit versions of Windows, the second on 64-bit versions, and the third on both.
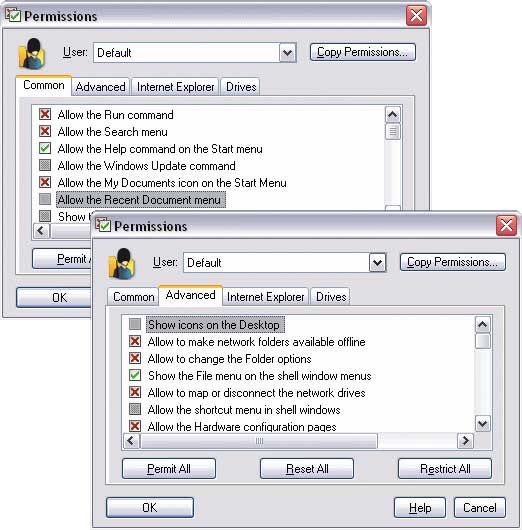
Restriction of access to personal data is carried out by hiding them (Fig. 11), setting the read-only mode or blocking. At the same time, hiding is implemented in two versions: you can make folders and files hidden or set them empty (Empty). In the second case, the folders will be visible, but when opened they will be empty, although in reality they contain information - this protection option is suitable for standard Windows folders, the complete hiding of which will indicate that information on the computer is blocked, which is undesirable. Protected folders without a password will not be available to other users of the system even when Windows is booted in safe mode, although this will require some settings in the program. If you forget your password, you can recover it using the free utility Emergency Recovery (http://www.winability.com/folderguard/eru.htm). Also implemented is the ability to run the program in Stealth Mode, in which its own shortcuts and files will be hidden.
Rice. 11. Hiding a Folder in Folder Guard
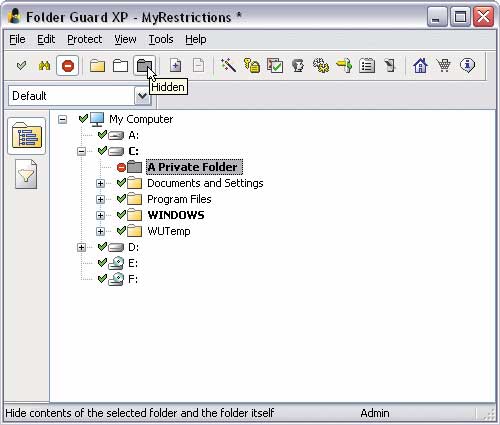
Using Folder Guard, you can also protect the basic OS settings from adjustment (Fig. 12) - in particular, block access to the properties of the taskbar, the Start menu and a number of other windows, prohibit saving display properties (if they have been changed), block changing properties folders and Internet Explorer settings, do not show icons on the desktop. And also prevent changes to critical parameters for the operation of the system by closing access to the control panel and setting a series of prohibitions: access to the system registry, adding / removing printers, using the Run command, etc. You can also hide certain discs in My Computer, Explorer, and the standard Open/Save dialog boxes and block CD/DVD burning. For different users, a different set of such restrictions is possible.
Rice. 12. Setting restrictions on access to Windows settings
in Folder Guard
Hide Folders XP 2.9.8
Developer: FSPro Labs
Distribution Size: 1.23 MB
Work under control: Windows 2000/XP/2003/Vista
Distribution method: shareware (30 day demo - http://www.fsprolabs.com/download/distr/hfxp.zip)
Price: $ 29.95 (in the Softkey.ru store - 400 rubles)
Hide Folders XP is a simple program to protect folders and files (Fig. 13) from unauthorized access by hiding and/or blocking them. Protected folders will not be available to other users, including the system administrator, even when Windows boots in safe mode. In this case, not only protected folders and files, but also folders containing them will be protected from deletion. And in order to prevent other users from guessing about the presence of protected data on the computer, the program can remove traces of installed protection and can hide itself (may not be displayed in the list of frequently downloaded programs, do not show the uninstall line in the control panel, hide itself in list of running processes, etc.).
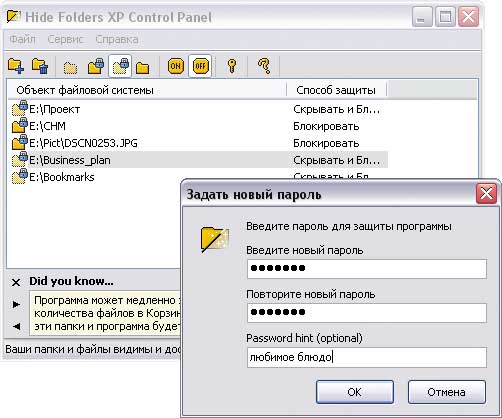
Rice. 13. Working with protected files in the Hide Folders XP environment